Feature updates
Add message search function
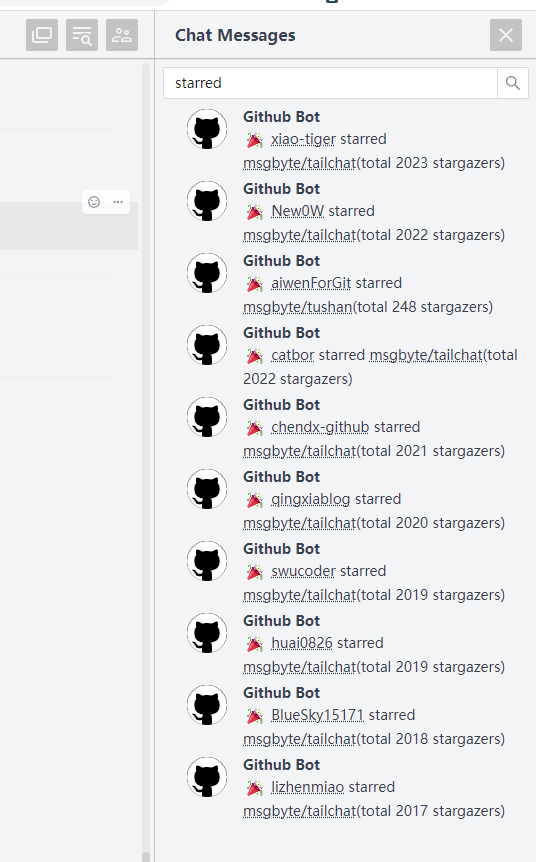
Searching for chat information in a session is now supported. Because of the search is directly request to database, there will be a timeout for performance reasons. That is, if the database does not return search results within 5 seconds, it will be considered a timeout.
Other updates
- HTTP requests add static caching to object storage and public files
- Add the environment variable
REQUEST_TIMEOUTto customize the rpc request timeout, the default is 10 * 1000, in milliseconds - AI assistant adds more tips
- Add telemetry information collection (can be turned off through environment variables)
- Fix issue with iam plugin not fitting light theme in login view
- Add defer tag to tianji script